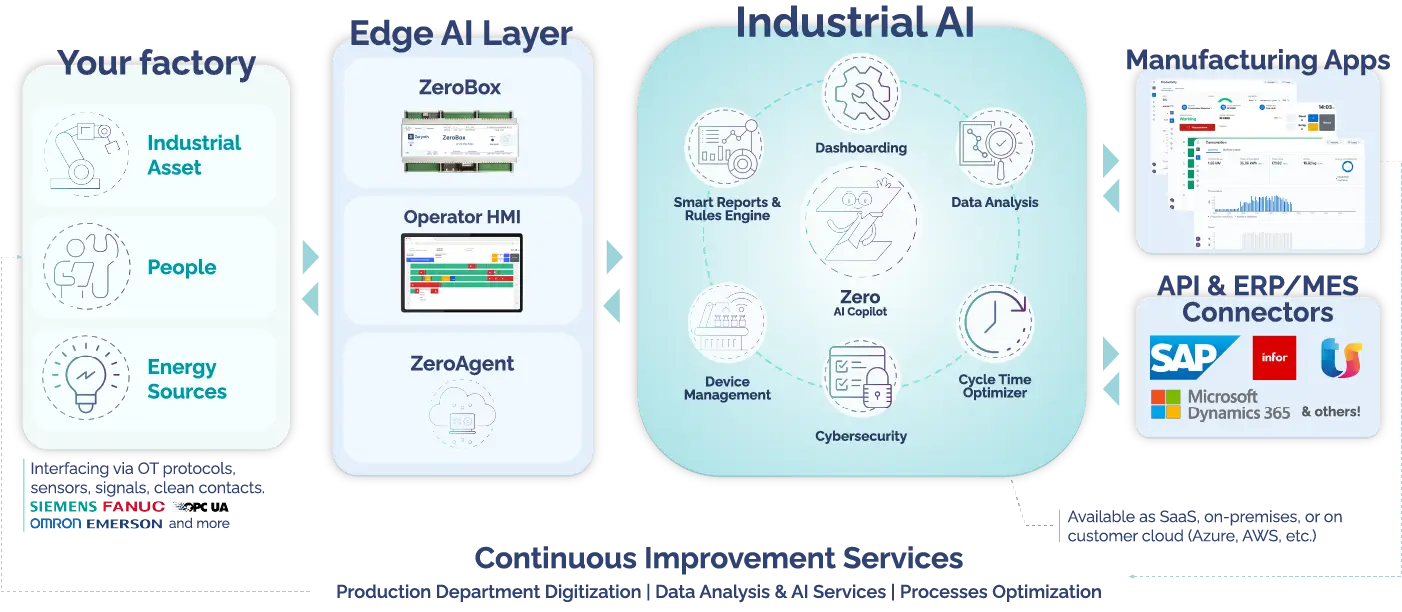
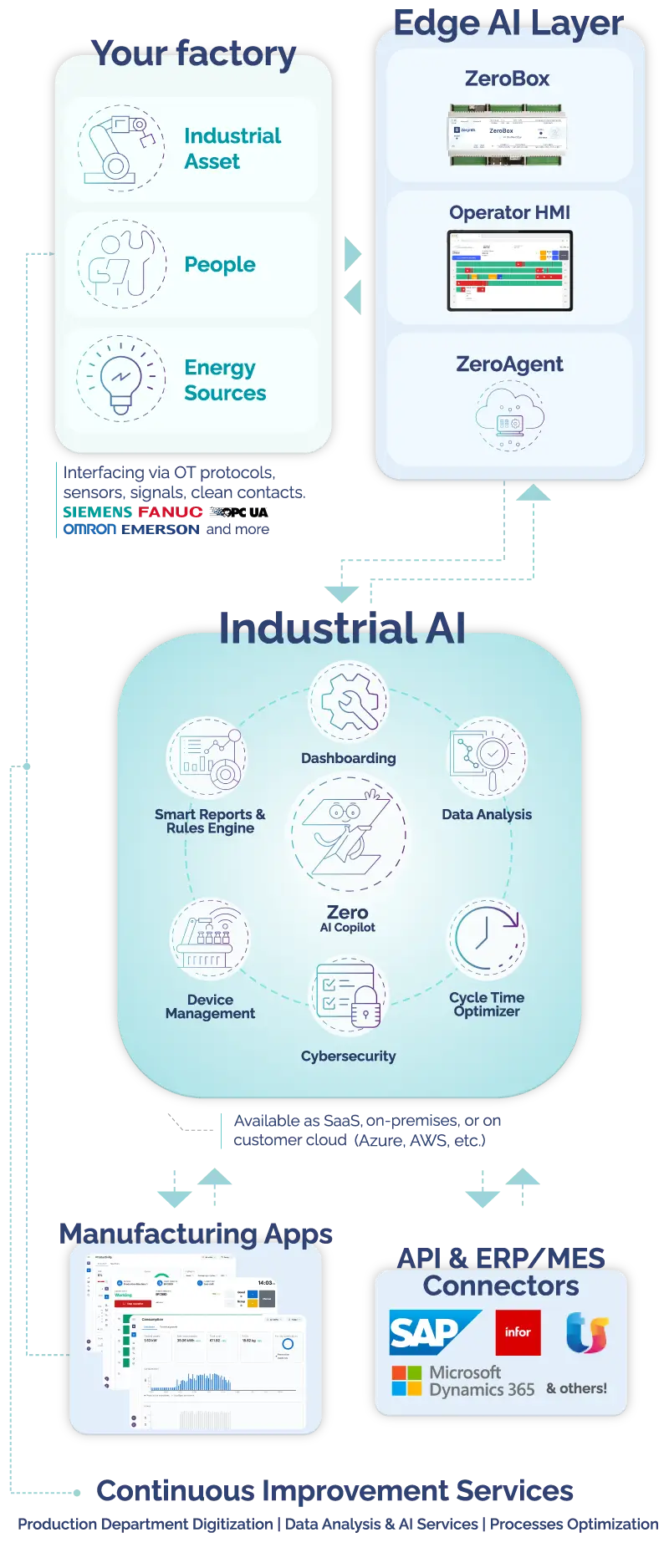
Secure Connection Manager
The system is equipped with a crypto element for secure device connectivity and data exchange through encrypted formats.
Secure Connection Manager
The system is equipped with a crypto element for secure device connectivity and data exchange through encrypted formats.
Secure Connection
The crypto element securely manages credentials to ensure they are not readable by third parties.
Blind authentication
Zerynth’s IoT devices are authenticated both on the cloud and on the device, guaranteeing secure and trusted communication between the two.
Encrypted data
Data is exchanged in an encrypted format with a unique key for each connection, ensuring secure and private communication between devices and the intended recipients.

Cloud authentication
Zerynth’s IoT devices are authenticated by the cloud using keys stored in the crypto element. Any other device cannot connect to the cloud to send data and thus simulate a Zerynth device. This solution helps to mitigate the risks of “man-in-the-middle” attacks and enhances the overall security of the system.
Device authentication
The device only receives data from the Zerynth cloud and cannot be contacted or manipulated by other systems. This solution reduces the risk of IoT device hacking, ensuring a higher level of security for the device.


Encrypted data
All data is exchanged in an encrypted format with a unique key for each connection. Private keys are never stored in the firmware of Edge devices or in the source code of our cloud platform. The private keys are generated by the manufacturer of the Crypto Element on the chip during production. We use the Crypto Element to store the network credentials of our devices, ensuring that they remain unreadable by third parties. This approach enhances the overall security of the system and mitigates the risk of unauthorized access to sensitive information.
Secure Connection
The crypto element securely manages credentials to ensure they are not readable by third parties.
Blind authentication
Zerynth’s IoT devices are authenticated both on the cloud and on the device, guaranteeing secure and trusted communication between the two.
Encrypted data
Data is exchanged in an encrypted format with a unique key for each connection, ensuring secure and private communication between devices and the intended recipients.

Cloud authentication
Zerynth’s IoT devices are authenticated by the cloud using keys stored in the crypto element. Any other device cannot connect to the cloud to send data and thus simulate a Zerynth device. This solution helps to mitigate the risks of “man-in-the-middle” attacks and enhances the overall security of the system.

Device authentication
The device only receives data from the Zerynth cloud and cannot be contacted or manipulated by other systems. This solution reduces the risk of IoT device hacking, ensuring a higher level of security for the device.

Encrypted data
All data is exchanged in an encrypted format with a unique key for each connection. Private keys are never stored in the firmware of Edge devices or in the source code of our cloud platform. The private keys are generated by the manufacturer of the Crypto Element on the chip during production. We use the Crypto Element to store the network credentials of our devices, ensuring that they remain unreadable by third parties. This approach enhances the overall security of the system and mitigates the risk of unauthorized access to sensitive information.
Main Features
1
Secure connection with Zerynth Platform Core.
2
Secure Element natively integrated.
3
Connectivity Stack based on TLS v1.2 e v1.3 standard protocols.
4
Data Encryption during the connection between Edge Device and Zerynth Platform.
5
idirectional Authentication and keys change based on ECDSA.